Some clients have the requirement to secure their online web application with a two stage login, this is called two factor authentication (or sometimes 2FA), and is usually split between something you have and something you know, usually with one of the two items expiring. Typical logons are a two stage or two screen logon process. Used extensively in the financial sector, it is not to difficult to setup and can be implemented for any industry sector if you need it.
2FA Security
Well from today, we can offer 2FA capabilities to any of our clients web applications on our portal. When they log in, if enabled, they will see the blue shield with a yellow 2FA padlock informing them that when they select their web application, they will be requested to complete the second stage of the 2FA process. This is so that clients may choose between typical one stage login and two stage 2FA for the more demanding security requirements.
How does it work
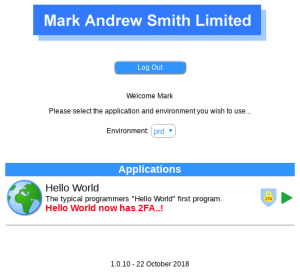
After entering your initial username and password, you are taken to the list of applications that you are entitled to access. In this example, I can only see the “Hello World” application. I can see in red that the MOTD (message of the day) is telling me that this web app now has 2FA. If I click on the green “play” button to start the application, instead of running the application, I am first taken to the 2FA login screen for you to be able to complete the secondary login stage that is a mandatory security requirement for this application.
Forms of 2FA Supported
In addition to the normal single stage username and password combination, we support the following forms of two factor authentication…
- Secure one time key code sent to an email address. *
- Secure one time key code sent to a SMS text number. *
- Secure secondary password stored as an encrypted hash.
Please note: those marked with a * are a one time key code generated on the fly, and have an expiry time out making a “man in the middle attack” impossible as they would have to know when and where you are likely to login. They would also need to know your unique session id, IP address, and your first screen username and password, which put simply all five items would not match. Once a 2FA code is used, or expires, the one time 2FA code is destroyed making the application very very secure. A new code is sent upon each login attempt.
If you need this level of security in your web application, then we are the company to provide it for you. Simple, stable and secure. Call us for more information and an informal chat on how we may be able to build your next software application securely.